FIDO Passkeys
The Importance of Biometric Binding
Understanding Risk Along the Security Chain
Agenda
- PKI on the Server
- Transport Security
- Device Storage
- Person Authentication: Biometrics
- Risk: Catastrophic vs. Lower Impact
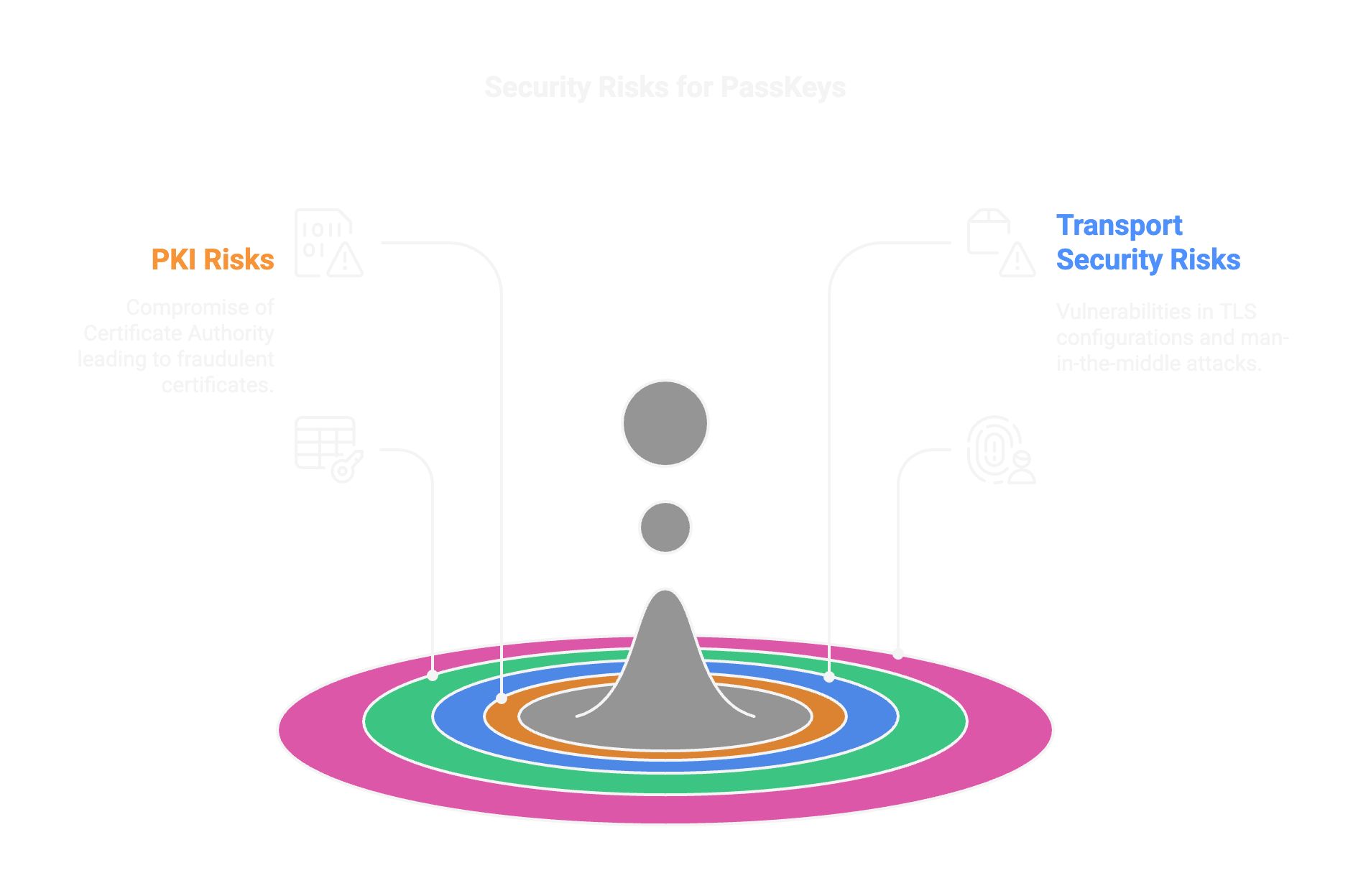
PKI on the Server
Risk Example
Compromise of a Certificate Authority.
Impact
Rare but catastrophic – attackers can impersonate the server.
Infrastructure risks here are infrequent, yet if they occur, the consequences are severe.
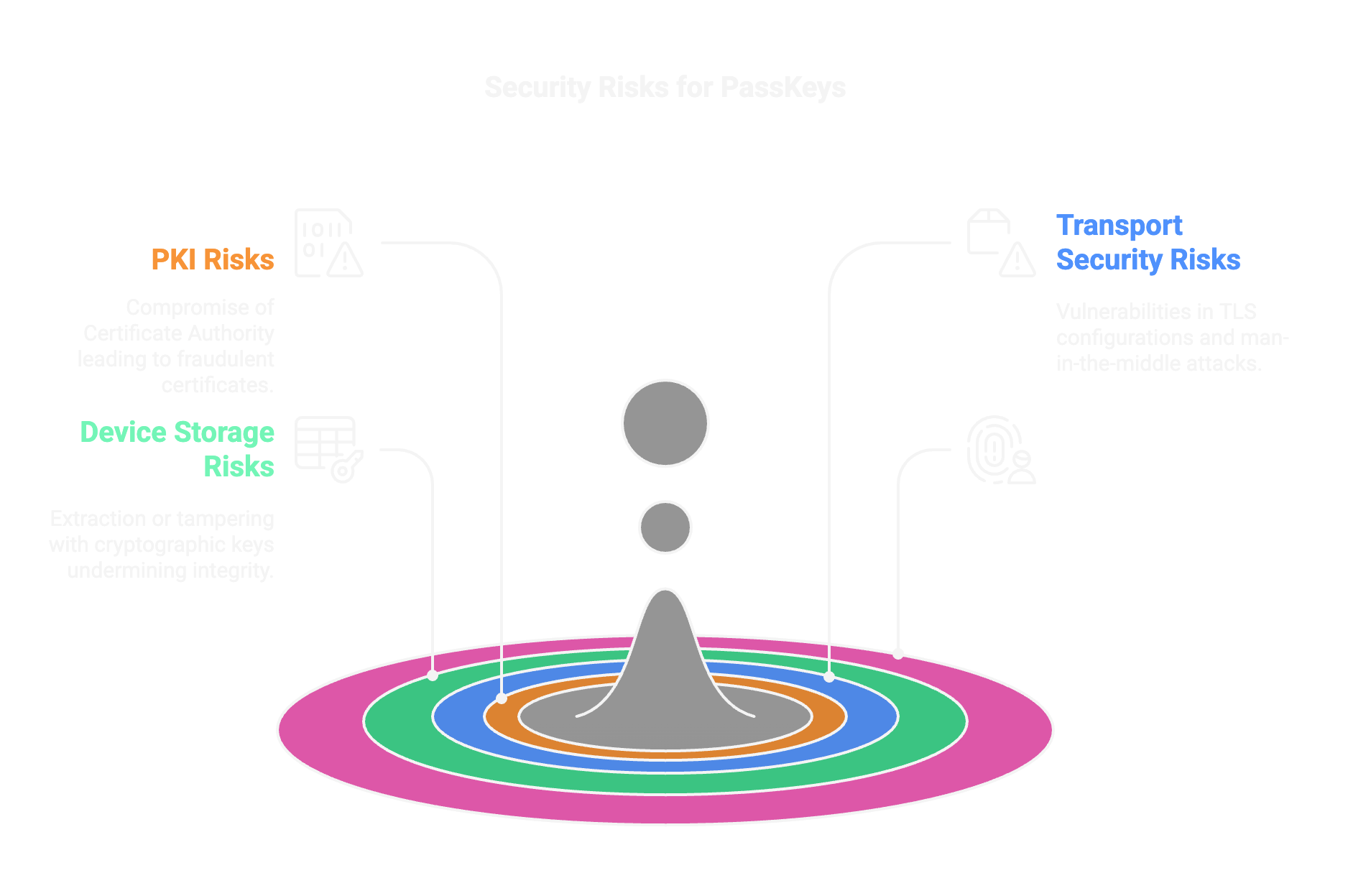
Transport Security
Risk Example
Exploitation of outdated TLS configurations or man-in-the-middle attacks.
Impact
Could allow interception of sensitive data.
These events are rare but, when they occur, can be severe.
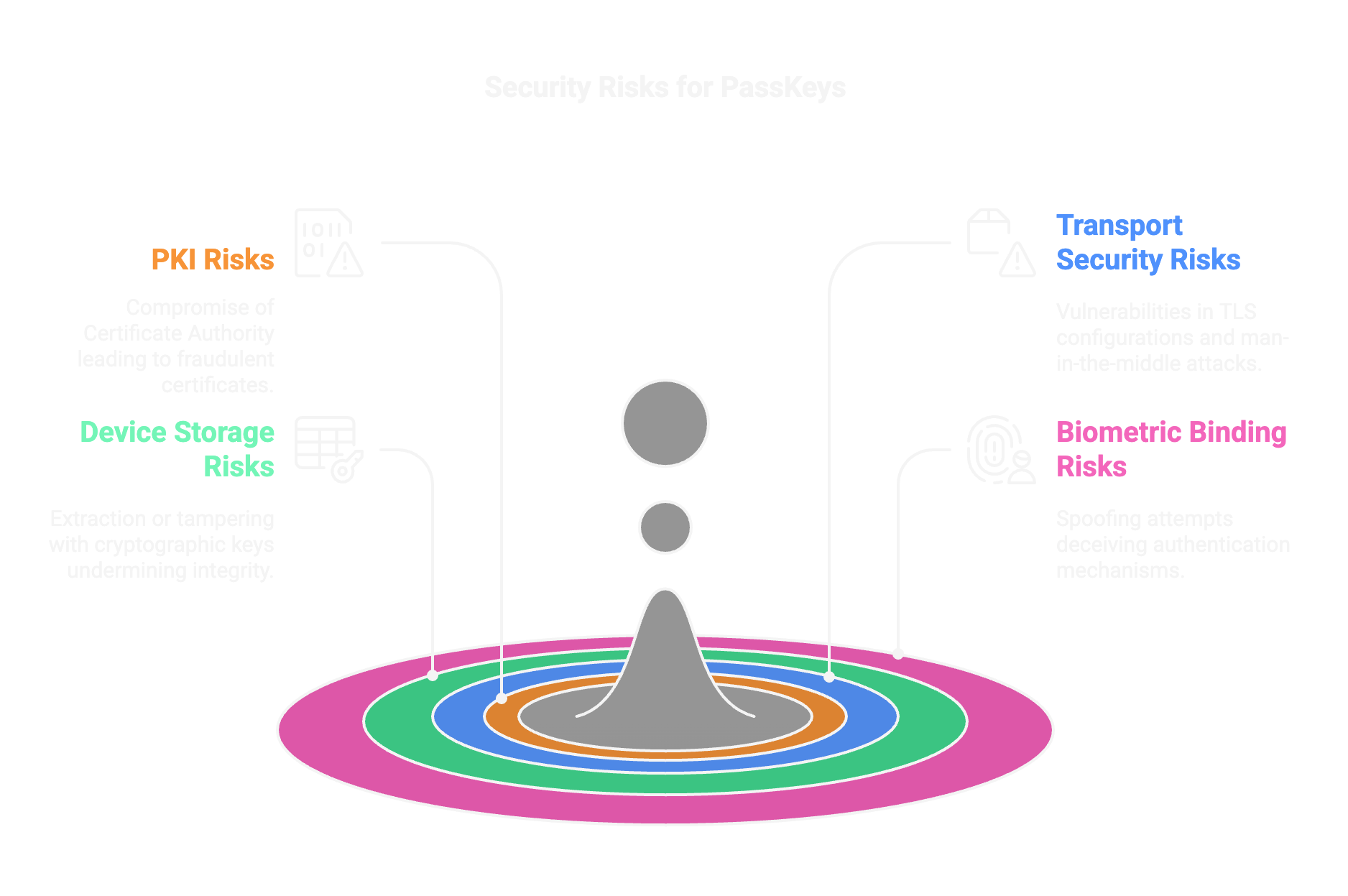
Device Storage
Risk Example
Extraction or tampering of cryptographic keys from secure device storage (e.g., secure enclave vulnerabilities).
Impact
If exploited, it can compromise the integrity of the passkey.
This is a critical point in the security chain with high stakes.
Person Authentication: Biometrics
Risk Example
Spoofing or presentation attacks against biometric sensors.
Impact
These issues are more common, yet typically localized with fallback methods.
Biometric binding is the final step that securely ties the cryptographic key to the user.
Risk Comparison
Infrastructure Risks
- PKI
- Transport Security
- Device Storage
Infrequent but catastrophic when they occur.
Biometric Risks
- Spoofing
- Sensor Attacks
More frequent, but lower impact with additional safeguards.
Conclusion
FIDO passkeys rely on a strong security chain—from server PKI and transport security to device storage.
While infrastructure risks are rare yet catastrophic, biometric issues occur more frequently but are generally manageable.
Together, they form a balanced and robust security approach.
Thank You!
Questions?
Copy of BixeLab Training
By Ted Dunstone
Copy of BixeLab Training
- 125



