Dr Ted Dunstone
🤝 Critical Importance of Trust
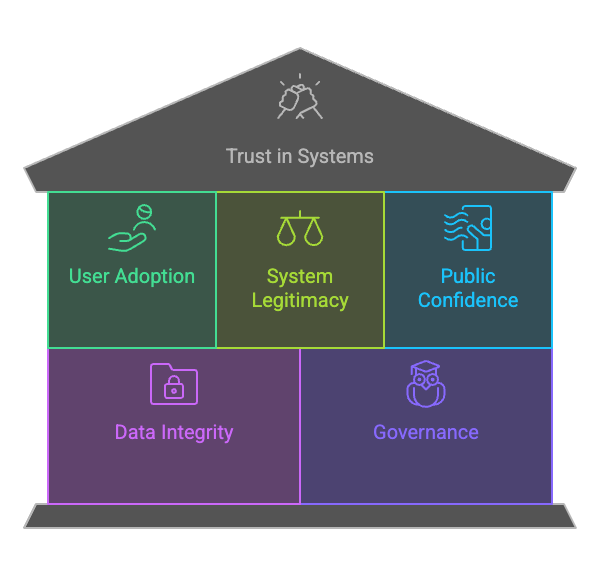
Trust is essential for user adoption and system integrity.
- Trust is the cornerstone for user adoption and system legitimacy.
- Transparency is key in building and maintaining public confidence.
- Data integrity and reliability
- Effective governance reinforces stakeholder and user trust.
Threats are continual and global ...
🔐 Foundational Cybersecurity Principles
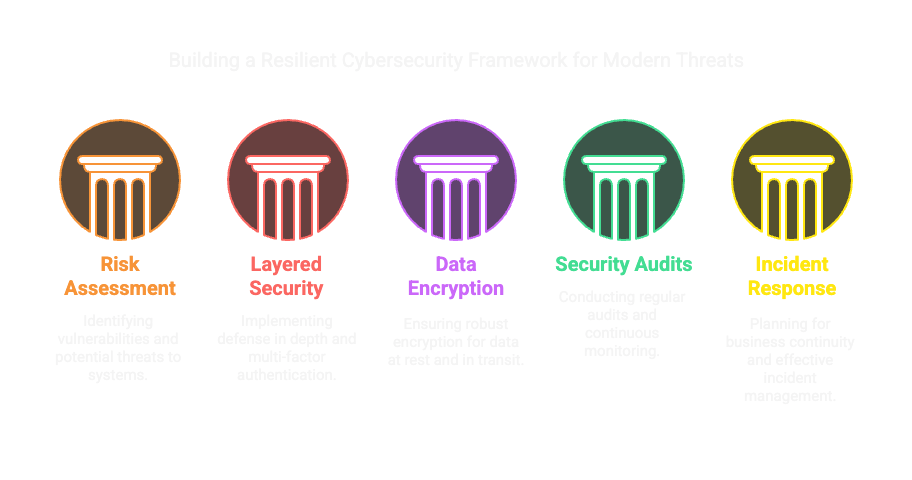
Implementing robust security measures is crucial for protecting digital identities.
- Best practices in secure software development and infrastructure hardening.
- Compliance with international cybersecurity standards and frameworks.

🔒 Access Control
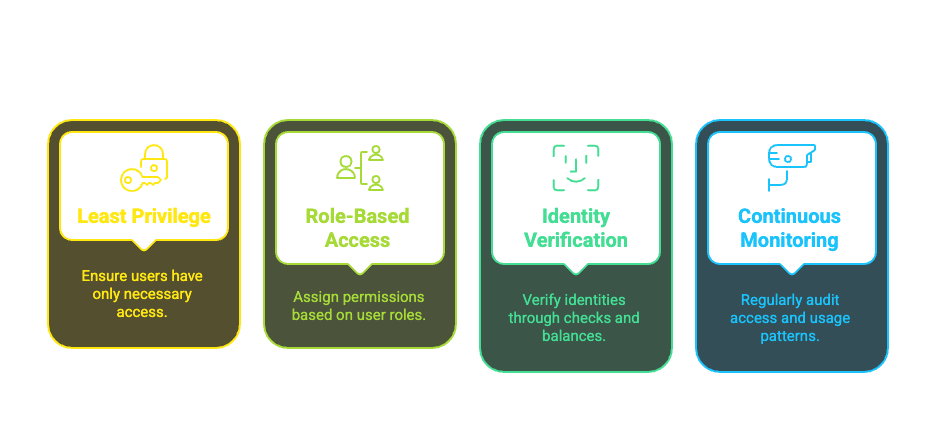
Combining identity verification with dynamic access control minimizes risk through layered security.
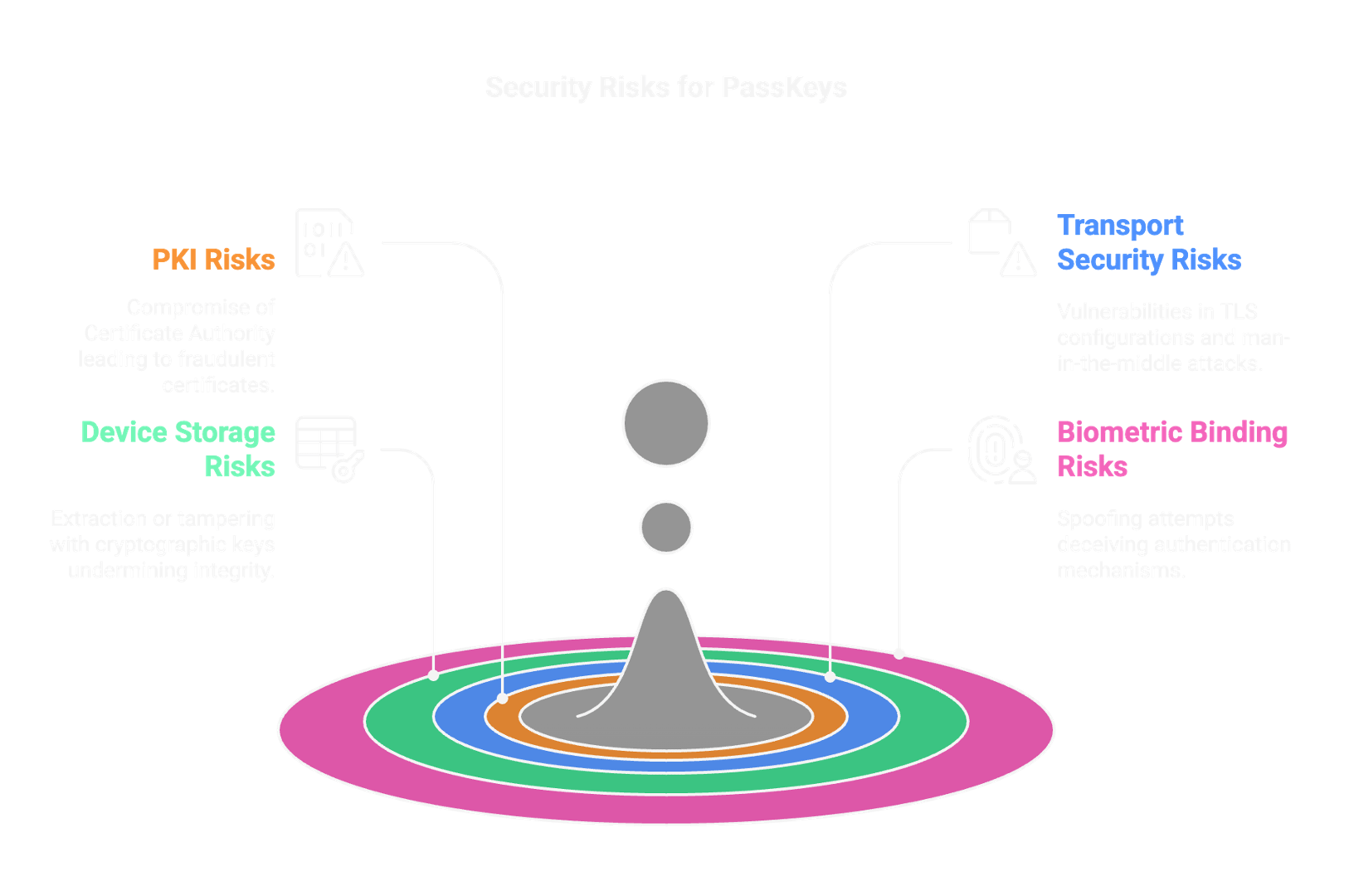
Digital ID Security Risks
Core
Edge
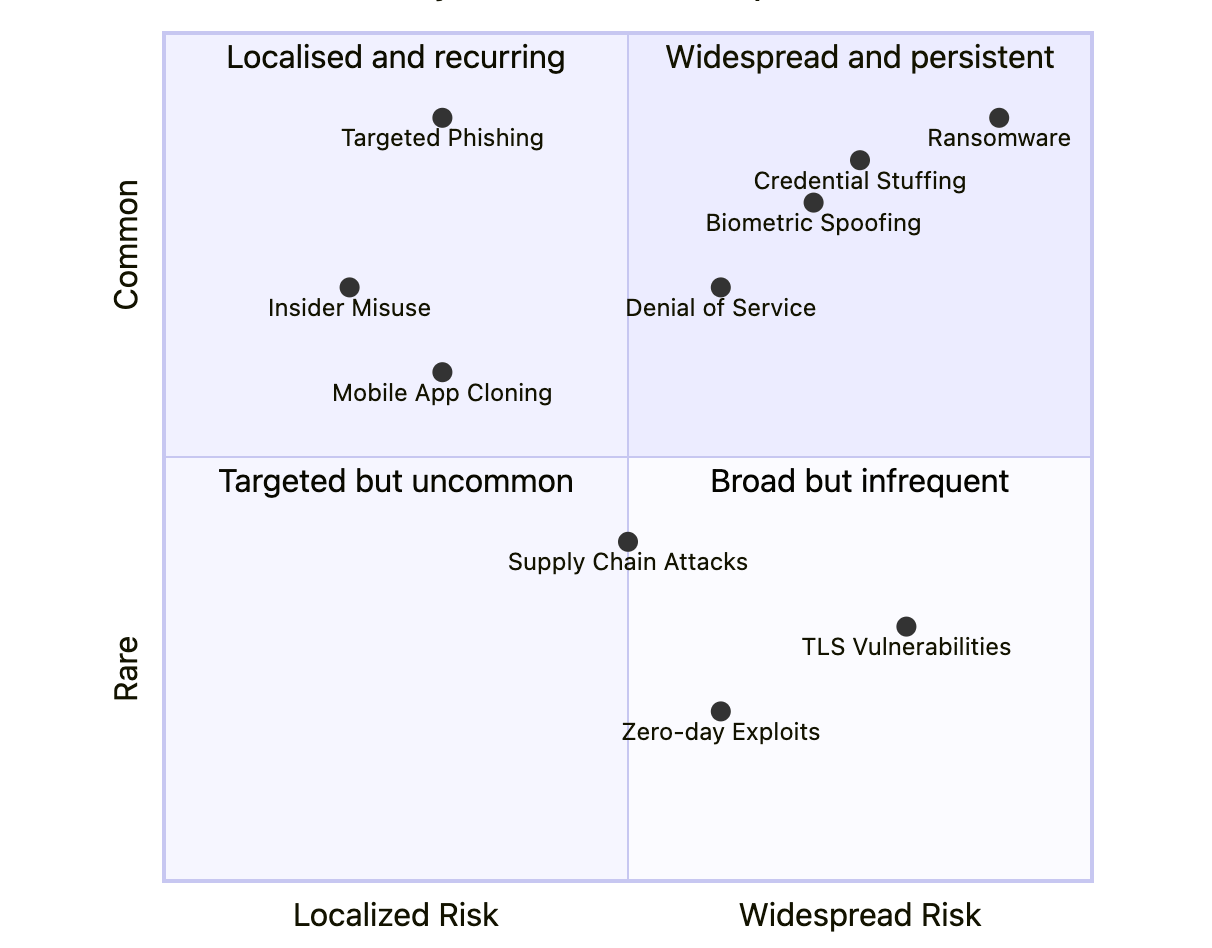

Digital ID Security Risks
A Map of Cyber Vulnerabilities

Biometric Spoofing
A Map of Cyber Vulnerabilities

Deep fakes
Biometric Spoofing
A Map of Cyber Vulnerabilities

Biometric Spoofing
Deep fakes
Deep fake video
Fake Documents
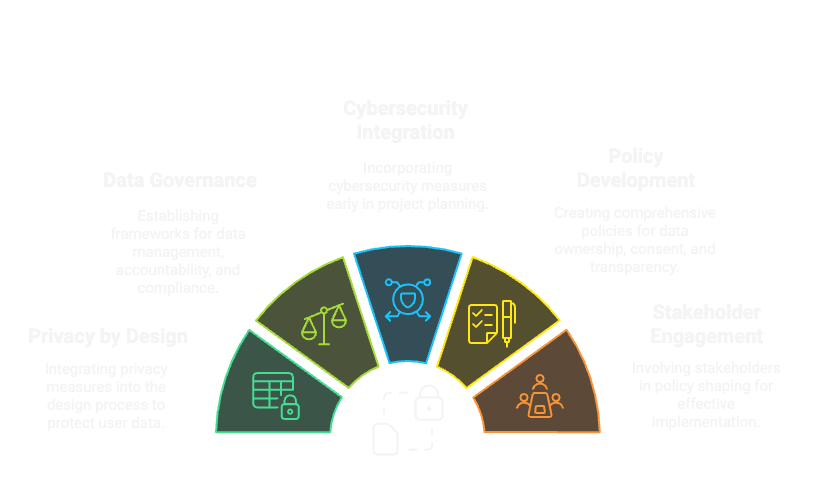
🕵️♂️ Embedding Privacy and Cybersecurity
Incorporate security and privacy considerations throughout both the policy development and implementation stages.
⚠️ Addressing Emerging Threats
Stay ahead of evolving cyber threats to protect digital identities.
Overview of emerging cyber threats, including AI attacks and IoT vulnerabilities.
- Global cybersecurity trends and regulatory changes.
- Balancing innovation and risk.
- Challenges in low-resource environments: limited infrastructure, budgets, and skills.
- Importance of international collaboration and capacity-building.
- Using emerging technologies to enhance resilience.
📅 Example Roadmap
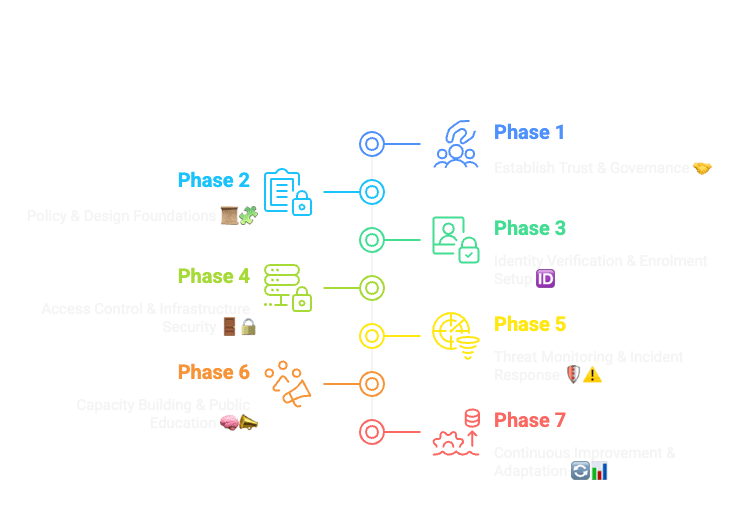
✅ Top 10 Checklist
- ☑ Build Public Trust: Ensure transparency, community engagement, and clear communication about Digital ID systems and data protection.
- ☑ Embed Privacy and Cybersecurity: Apply “privacy by design” and “security by design” from planning to implementation.
- ☑ Implement Strong Access Controls: Use role-based or attribute-based access control and the principle of least privilege, supported by background checks and reviews.
- ☑ Ensure Secure Identity Verification: Use reliable identity sources and anti-fraud measures, especially at enrolment.
- ☑ Use Robust Encryption: Encrypt personal data and limit data retention with secure storage practices.
✅ Top 10 Checklist
- ☑ Regularly Monitor and Audit System Activity: Continuously check for anomalies and keep audit trails to detect misuse early.
- ☑ Plan for Incident Response and Recovery: Create and test a national response plan for cyber threats to Digital ID systems.
- ☑ Align with Global Standards and Regional Norms: Follow frameworks like ISO/IEC 24760, NIST guidelines, and relevant data protection laws.
- ☑ Account for Local Capacity and Resource Constraints: Select scalable solutions for low-resource environments and plan for gradual implementation.
- ☑ Invest in Capacity Building and Public Awareness: Train staff and partners on security practices, and educate the public on safe Digital ID use.
Cybersecurity Initiatives for ID Systems
-
Cybersecurity Diagnostics and Governance: Helps countries assess cybersecurity maturity and set up governance frameworks for cybercrime and cybersecurity. Learn more
-
Risk Management and Critical Infrastructure Protection: Works with governments to manage cybersecurity risks, safeguarding critical infrastructure in finance, health, and telecom. Read further
-
Cyber Incident Response: Aids countries in preparing for and responding to major cybersecurity incidents, enhancing national response teams. More information

Privacy and Security by Design Approach
-
Legal Frameworks: Highlights the need for data protection and privacy laws to secure individual data and rights. Details here
-
Operational Security Controls: Suggests measures to ensure the security of ID facilities and data centers. Explore more
-
Cybersecurity Program: Recommends building capacity in ID authorities to safeguard assets and manage cybersecurity risks. Guidance available

Tools and Resources for Practitioners
-
ID Enabling Environment Assessment (IDEEA): A tool to assess a country's ID systems and legal frameworks. Access the tool
-
Technical Standards Catalog: Guidance on adopting standards for ID system interoperability and security. View the catalog
-
Costing Study and Model: Insights into costs of ID system designs for budgeting. Learn more

Conclusion
Cybersecurity is constantly evolving and remains a fundamental aspect of our systems.
- Ensure it is embedded throughout the entire lifecycle
- Procurement / Design / Pre-Production / Production
- Ideally, obtain independent assurance and testing
- Implement proactive measures for monitoring and mitigation
Questions