The Use of Data to Keep Users Safe
Navigating Identity, Trust & Threats in the Digital Age
Presented by
Dr Ted Dunstone and Brett Feldon.



Why Identity Data Matters
- Digital Expansion: As our digital lives grow, identity becomes increasingly complex and vital.
- Trust Ecosystem: Financial services are important to a growing trust ecosystem, comprising multiple standards and organisations (e.g., AGDIS, FIDO, FVS, VCs, ConnectID).
- High Stakes: Threat landscape is changing - mostly for the worse.

What Counts as Identity Data?
- Biometrics: Facial recognition, voiceprints, fingerprints.
- Credentials: Passwords, PINs, passkeys.
- Biographic Details: Name, date of birth, address.
- Behavioral Patterns: Typing rhythm, device usage.
- Transaction Data: Information about activities between customer and bank, such as logins, payments etc
- Combined Use: Creating secure, frictionless services through multi-factor authentication.







Which one is deep fake?
Biometrics in Banking
- Facial Recognition: Used during onboarding processes, authentication.
- Voice Authentication: Secure customer verification, often in call centers.
- Fingerprints: Used for on-device authentication.
- Passkeys & FIDO Standards: Enhancing secure payment systems.
- Real-World Applications: Organisations leverage these technologies for enhanced security.
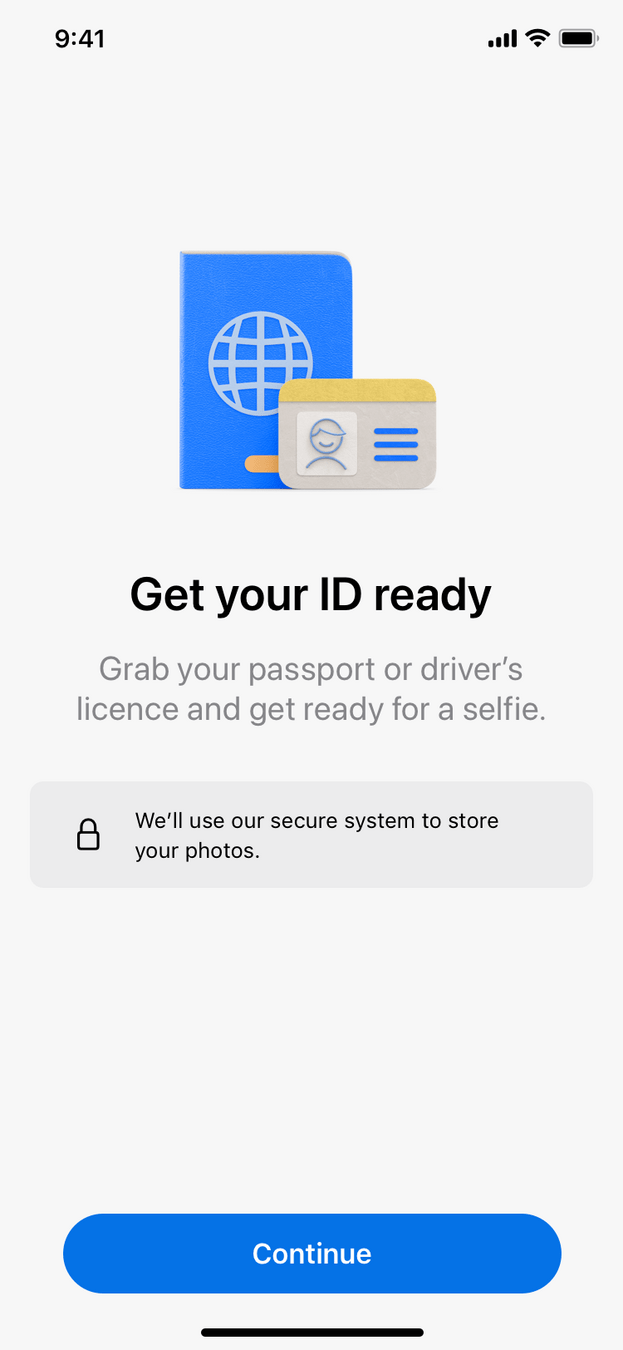


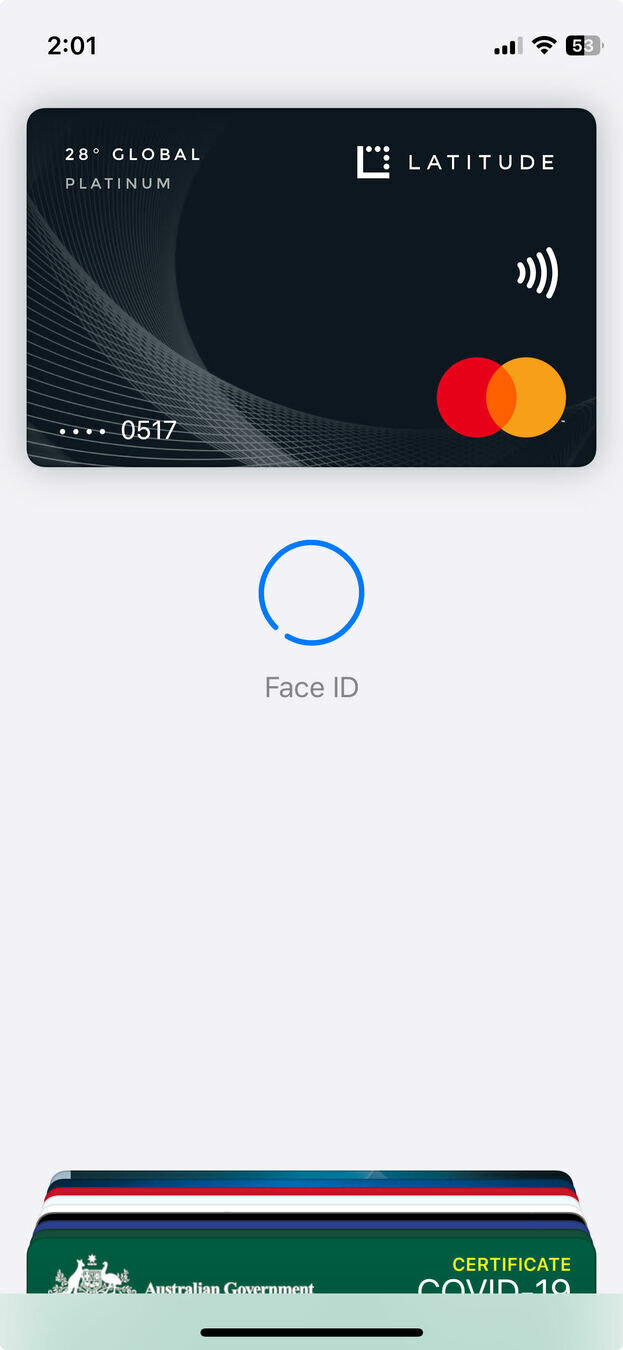
Privacy and Ethical Challenges
- KYC Obligations vs. Consent: Balancing regulatory requirements with user consent.
- Data Minimization: Collecting only necessary information.
- Surveillance Concerns: Addressing customer perceptions and building trust.
- Ethical Frameworks: Implementing guidelines to navigate these challenges responsibly.
Emerging Threats
- Document Fraud: AI-generated fake documents challenging verification processes.
- Deepfakes: Synthetic media used for impersonation and fraud.
- Synthetic Identities: Combining real and fake information to create new identities.
- Human Interaction Vulnerabilities: Frontline staff targeted through sophisticated schemes.


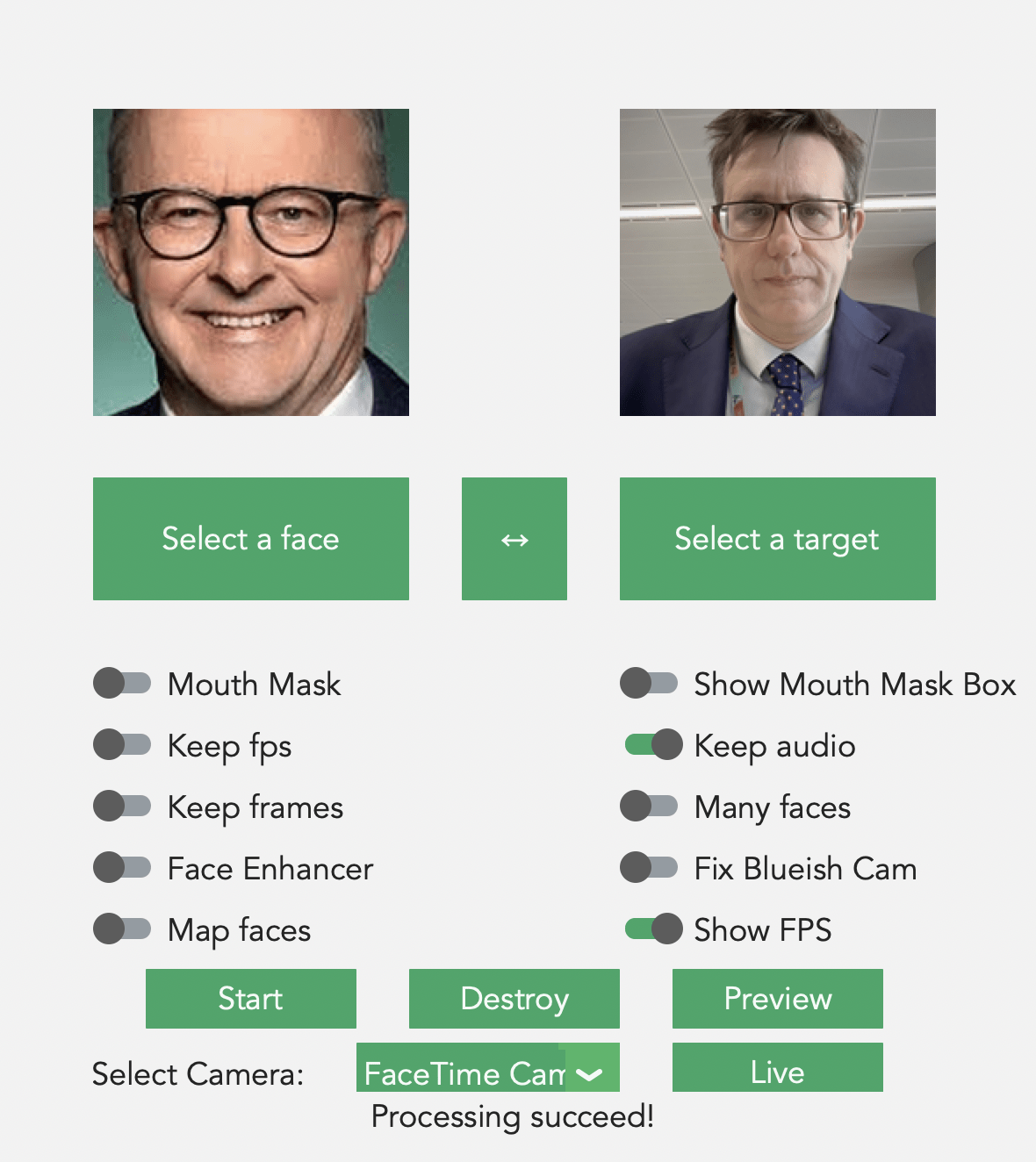

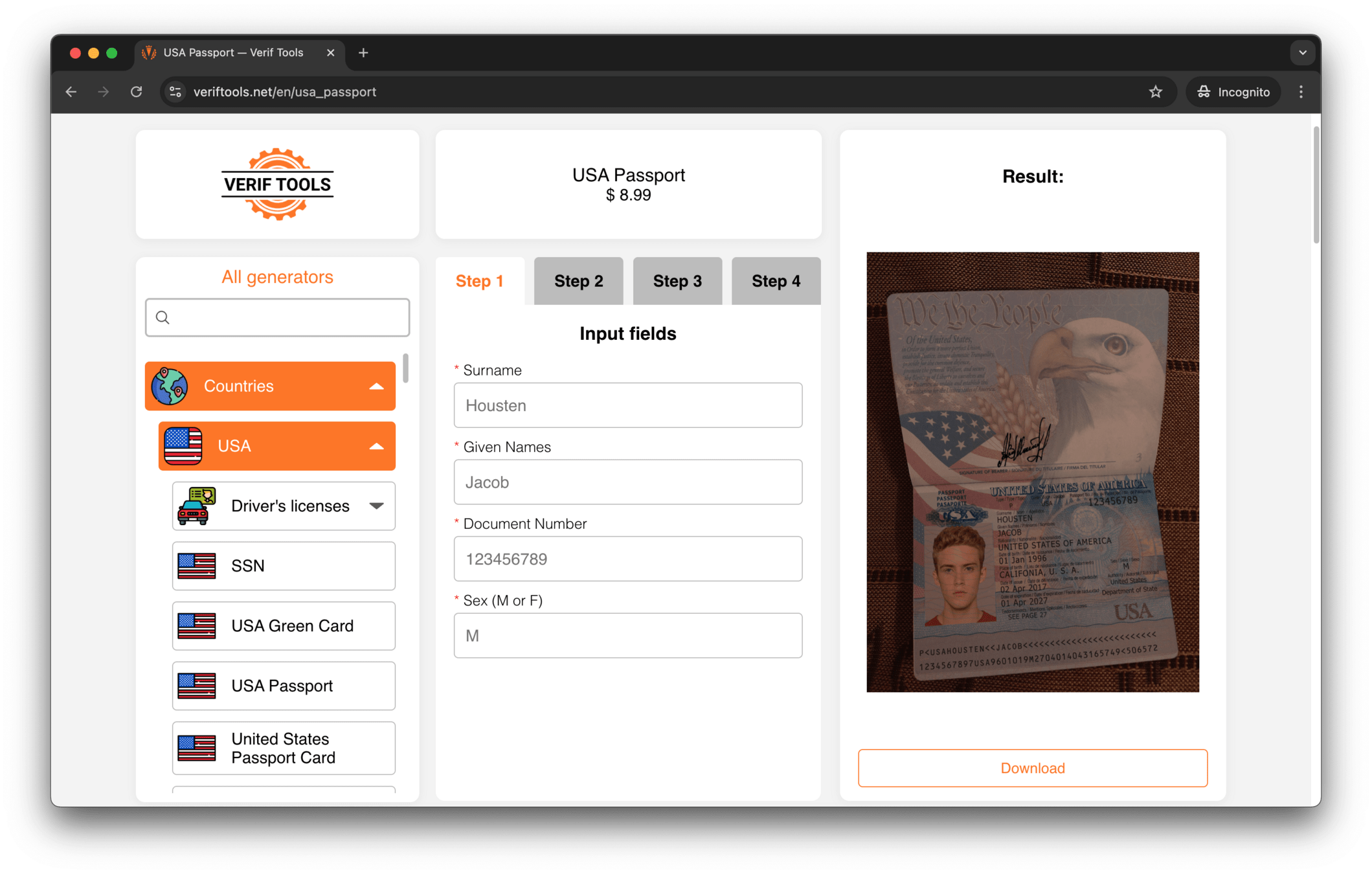
Building Trust Through Testing and Training
- Skilled Personnel: Ensuring staff are trained to handle advanced threats.
- Independent Validation: Third-party assessments to verify system integrity - accuracy, liveness, injection, document authenticity.
- Robust Assurance Processes: Embedding security checks at every stage of digital identity service delivery.
- Continuous Improvement: Regular re-evaluation to adapt and respond to evolving threats.

Conclusion
- Integrated Approach: Combining technology, ethics, and user-centric design to safeguard identities.
- Proactive Measures: Staying ahead of emerging threats through continuous learning and adaptation.
- Collaborative Effort: Engaging stakeholders across sectors to build a secure digital future.
The Use of Data to Keep Users Safe - Generic
By brettfeldon
The Use of Data to Keep Users Safe - Generic
- 29